Metasploit 使用技巧汇总
msf的使用技巧,持续更新。
msf 升级更新
msf本身不支持内部更新,需要用apt、yum update后安装更新。
# Ubuntu apt-get install metasploit-framework -y # Centos yum install metasploit-framework -y
msf加载最新的payload/exp
升级msf版本并不会更新刚出的exp。
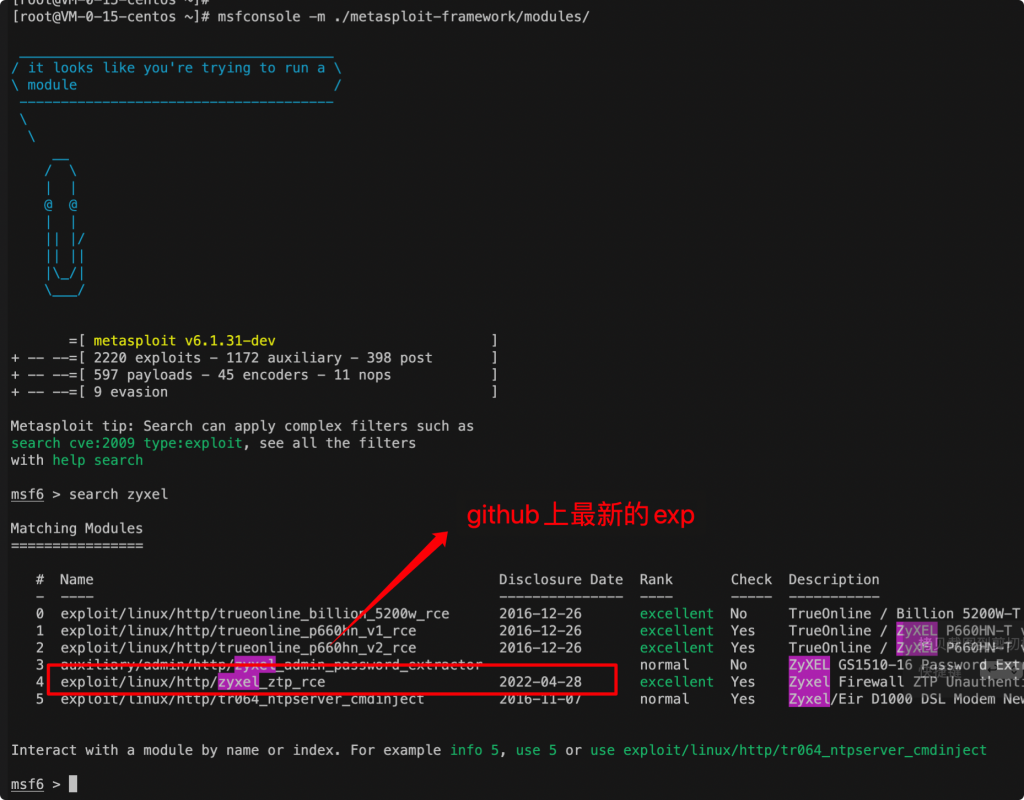
可以直接从 github 上git clone 最新的版本下来。
git clone https://github.com/rapid7/metasploit-framework.git msfconsole -m ./metasploit-framework/modules/
msf输出控制台日志到文件
msf6 > spool Usage: spool <off>|<filename> Example: spool /tmp/console.log msf auxiliary(udp_sweep) > spool log.txt # 启用spool,将输出信息写入到log.txt [*] Spooling to file log.txt... msf auxiliary(udp_sweep) > exploit [*] Sending 13 probes to 172.16.80.0->172.16.80.255 (256 hosts) [*] Discovered Portmap on 172.16.80.2:111 (100000 v2 TCP(111), 100000 v2 UDP(111), 100005 v3 UDP(1058), 100005 v2 UDP(1058), 100005 v1 UDP(1058), 100005 v3 TCP(1058), 100005 v2 TCP(1058), 100005 v1 TCP(1058), 100003 v3 UDP(2049), 100003 v3 TCP(2049)) ... ... msf auxiliary(udp_sweep) > spool off # 停止spool [*] Spooling is now disabled
Metasploit 默认运行exploit/run无法保存控制台输出信息,查看不是很方便。如果指定日志文件,退出msf后会输出到当前目录下,也可以指定日志的绝对路径。
赞赏 微信赞赏
微信赞赏 支付宝赞赏
支付宝赞赏
发表评论